Automated setup and designed for DevOps platforms
The core of EntraOps is a PowerShell module and works on any platform which supports PowerShell Core. It can be also executed locally within an interactive session. It’s optimized for being used in a DevOps environment and includes an automated setup for GitHub and Federated Credentials. This also allows you to take advantage of Git, to compare changes of your privileged assets.
Identify, classify and protect your privileged assets
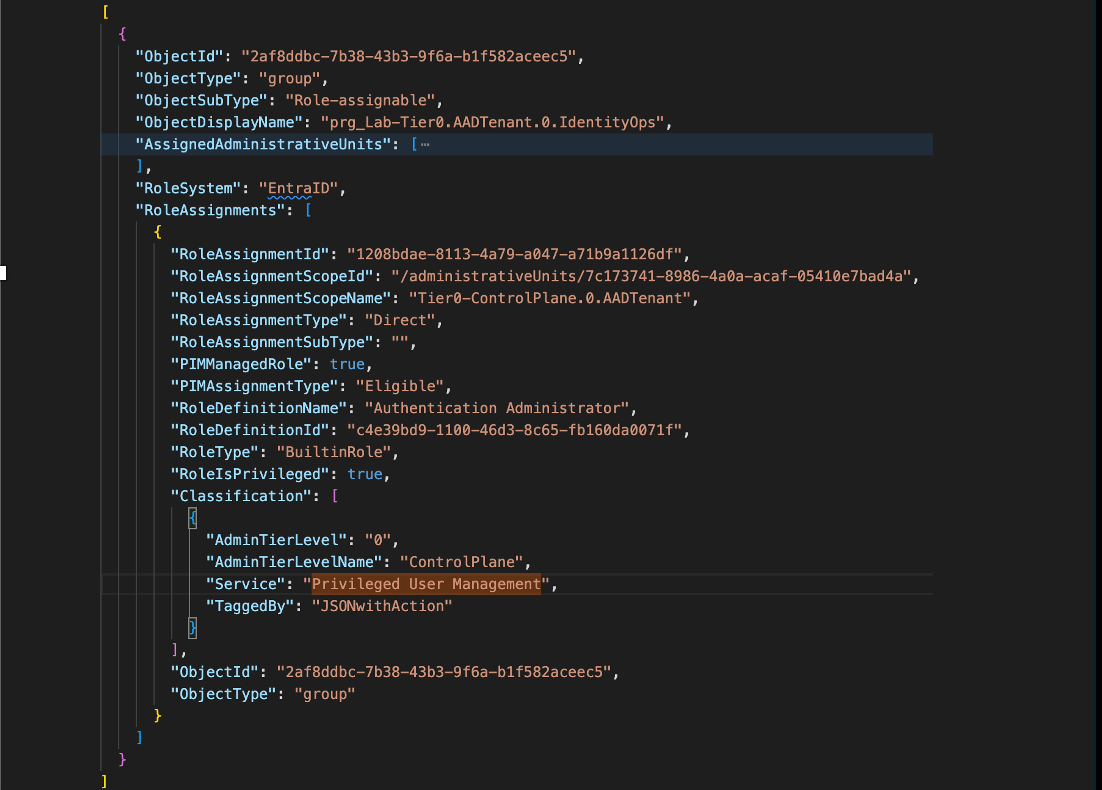
Get insights about privileged users, groups and workload identities with eligible, permanent, time-bounded and nested role assignments in Microsoft Entra. EntraOps uses a full customizable and flexible classification model. It provides templates (defined in JSON) to identify privileges and tiered administration based on Enterprise Access Model. In addition, the identified privileges can be automatically assigned to Conditional Access targeting groups and (Restricted Management) Administrative Units for managing and protecting them.
Automatic update on Control Plane resources and scope
An optional feature allows you to collect data from other sources to identify high-privileged assets. For example, using classification of critical assets in Microsoft Security Exposure Management. The scope of the privileged principals with access to those assets will be identified as Control Plane and therefore any delegation in Microsoft Entra to manage them. This allows to identify critical scoped role assignments on Groups, Service Principals or Administrative Units.
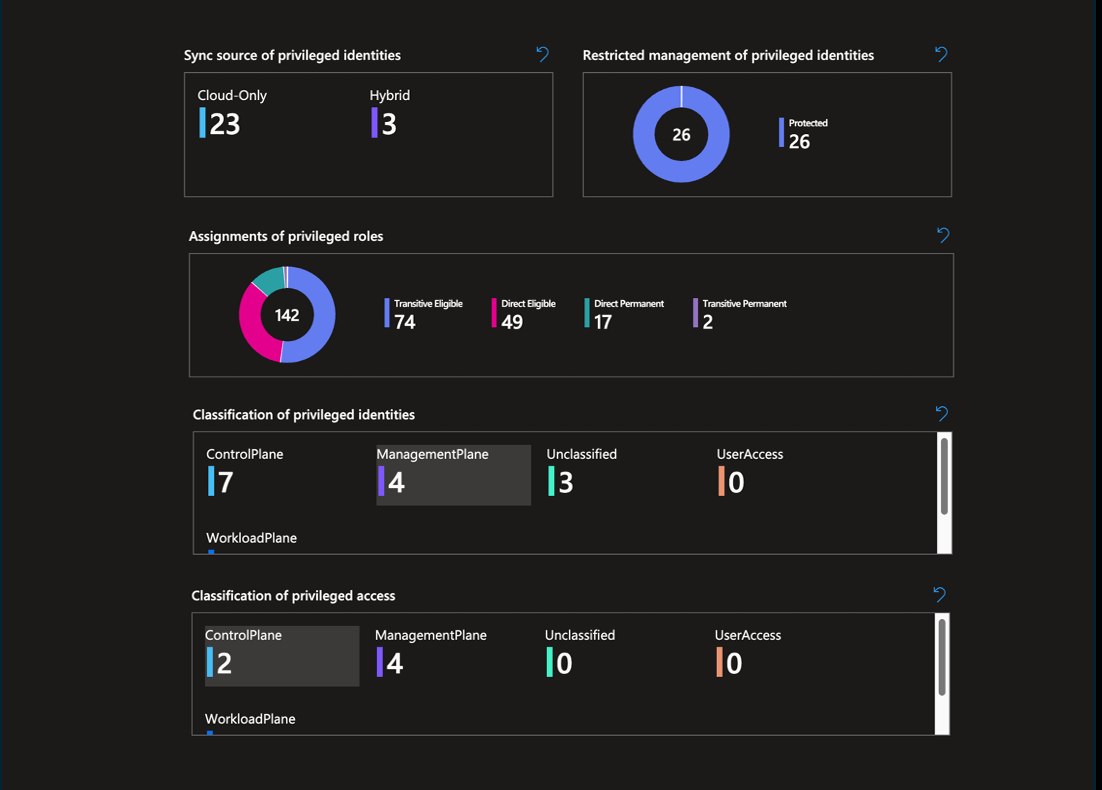
Analysis and visualization of privileged classification
Ingestion to classified privileges with detailed data to Log Analytics Workspace or Sentinel WatchList is already integrated. This allows to use the EntraOps data for advanced hunting or other integration for entity enrichment. The provided KQL examples shows how to correlate classified privileges by EntraOps with Microsoft Security Exposure Management data. A workbook template to visualize results of all classified roles is available which allows to identify “tier breach”. This allows you also to compare classification of privileged objects (based on custom security attribute) with their classified privileged access (identified by EntraOps).